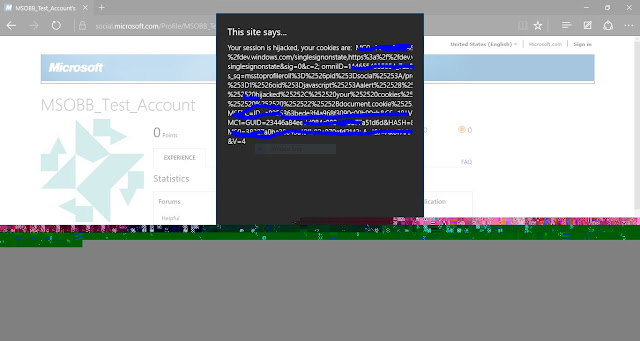
I had found a reflected XSS issue Microsoft, below is the report.
------------------- Email starts here -------------------
Vulnerability Type: Non Persistent XSS
Abstract: The affected url is vulnerable to Non-persistent XSS due to which an attacker is able to take over Microsoft account of logged in user.
Affected Url: https://www.microsoft.com/en-us/research/search/?q=<script>;prompt()<script>
Payload: <script>;prompt()</script>
Vulnerability Impact Senario: With Non Persistent Cross Site Scripting(XSS) an attacker can create custom URL with cookie stealing code on visiting which a user's cookie can be stolen and his account can be hijacked.
Vulnerability Reproduction Steps(POC):
1. Visit the URL "https://www.microsoft.com/en-us/research/search/?q="
2. With the parameter "q=" we can inject our payload.
1. Visit the URL "https://www.microsoft.com/en-us/research/search/?q="
2. With the parameter "q=" we can inject our payload.
Brief description of the issue:
Proof of Concept:
Hall Of Fame: